# Build scrambled openvpn deb packages # Based on # and # scramble xor patch # # # Built on a digitalocean VPS # 512 MB Memory / 20 GB Disk / – Ubuntu 14.04.5 x64. I've been trying to make openvpn client work on ubuntu 20.04 but could not. This is the config I'm using on a mac, windows and my ubuntu machine: client dev tap0 proto tcp dev-node MY-VPN //only on windows remote my.server.ip 12974 resolv-retry infinite nobind persist-key persist-tun ca ca.crt cert cert.crt key key.key cipher AES-128-CBC comp. OpenVPN installer for Debian, Ubuntu, Fedora, CentOS and Arch Linux. This script will let you setup your own secure VPN server in just a few seconds. 6 thoughts on “ Build scrambled openvpn (2.4.1) linux deb packages for VPS using sbuild ” soko prens April 2, 2017 at 8:50 pm. Hi thank you for great tutorial but. I have question, should ı to do ” This is how we build from start” section?
- Dynamic DNS.
- OpenVPN.
- AFP Server (for OS X).
- SMB server (for Windows and Linux).
- Reliability (Backups).
In part 1 we configured DNS name for our home server, which we can use outside of our network to find it. After that you have an option to make some ports available for public access, like Remote Desktop, ssh and VNC server and just protect these services by password. This solution is not very secure, because somebody can attack you in two different ways: brute-force your password or use Man-in-the-middle attack. You probably think that because you are not so important that nobody has a reason to attack you. This is not true, illegal botnets always are looking for new members.
OpenVPN
So what you can do for that? You can use OpenVPN. It protects you from brute-force attach by just not accepting clients with invalid certificates and it does not allow to perform Man-in-the-middle attack, because your client always will verify server certificate (just make sure to keep your keys in safe place).
Beta: Tunnelblick 3.8.6beta01 (build 5680, macOS 10.10+, (mixed Intel-64, M1), notarized) released 2021-04-11 Release Notes SHA1.
The other reason to use OpenVPN is to protect yourself when you use public WiFi networks from Session hijacking. To do that you can connect to your own home server, and transfer all network traffic to your home server using encrypted channel, so nobody on this public WiFi network will see what you are doing, they will only see that you are connected to home server.
Prepare OpenVPN server
On Ubuntu you can switch to root session, because these steps will require to perform a lot of root commands, you can do it by
You can read detailed explanation of all steps on Ubuntu Server Guide → VPN,
In file vars you just need to adjust next lines
After that create your Certificate Authority
Generate server certificate
Every time when you will need to generate certificates you need to be sure that you did source vars. If you still in the same session as we started, just continue to execute commands
All your keys and certificates will be generated in /etc/openvpn/keys folder. Keep it secure!
For the server you will need to use 4 files which you should copy to folder /etc/openvpn/ (this is where OpenVPN is looking for config files by default)
Generate client certificates
After that you can generate as many client certificates as you need. Better to use one certificate per client, so if it will be compromised you can easily revoke it.
You can come back to this step any time when you need to generate client certificates, just don’t forget to do source vars before that
For client you only need to use next files:
You will need to transfer these files with configuration later to your devices.
Setup OpenVPN server
In this example I’m going to setup two VPN servers, because in most cases I need to just get access to the home network without redirecting my Internet thought VPN. So one VPN network will allow me to redirect Internet traffic and other one will allow me to get access to home network. And yes, you can use both at the same time.
… to safely browse Internet on public networks
This one is very simple to do, just copy sample configuration files and do some adjustments
Tunnelblick For Ubuntu Download
Save server.conf as a backup file and rename it to something more meaningful for you
Edit /etc/openvpn/server-internet.conf file
Most important settings which we want to modify
All other settings you can keep by default or modify after reading manual.
Restart openvpn service to load this configuration
You can verify that you now have tun0 network interface
The last step is to configure IP forwarding on Ubuntu
First we need to enable IP forwarding by
To persist this setting between restarts you also need to edit /etc/sysctl.conf and uncomment/add this line
After that add couple of rules to iptables, don’t forget to update your network mask 10.8.0.0/24 and Ethernet interface eth0 (probably you will have eth0 by default)
To persist these settings we need to save them to file
And auto load them on boot, edit /etc/network/interfaces file
To include line which will load iptables.rules
Server is ready for VPN. But before configuring clients let’s add one more VPN configuration, which will allow us to connect to home network.
… to get access to home network
Let’s setup second configuration
Where we will specify
Restart openvpn service
Verify that new interface created (probably tun1)
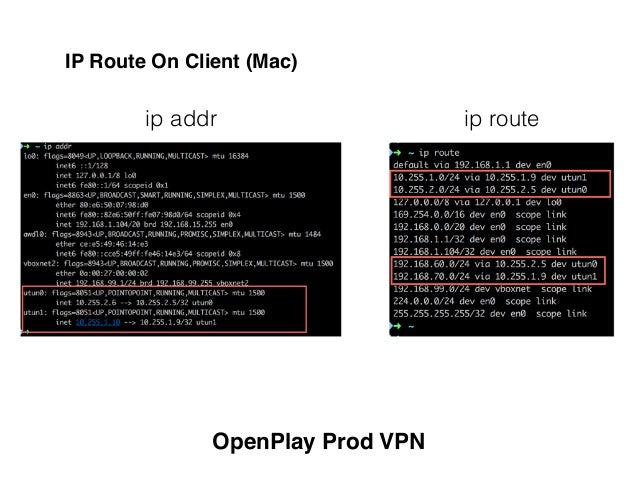
After that we need to configure iptables again (verify network interface names tun1 and eth0, also VPN subnet and home subnet)
And don’t forget to persist ipconfig settings. If your configured previous VPN than just save it again
No need to modify /etc/network/interfaces again.
Ok, so clients know how to communicate to devices on your home network, but devices on your home network don’t know how to get back to connected to VPN clients. To do that you will need to update Routing Tables on your devices, the easiest way to do that will be to add them to your home router (if it supports that).
This is how it looks in my case, where 10.111.0.0 - subnet of my VPN network (10.9.0.0 should be in our example) and 192.168.1.10 - address of my Ubuntu Server (OpenVPN server) in my home network
Setup OpenVPN client
Does not matter which client you are going to setup you always need 4 files
Linux client
Install openvpn
Copy example configuration
Download ca.crt, mylinuxclient.crt and mylinuxclient.key from OpenVPN server (mylinuxclient.* files are generated with ./build-key mylinuxclient) and copy them in /etc/openvpn/.
Adjust client.conf
Tunnelblick For Ubuntu Windows 7
Most important settings are
Restart openvpn service
Verify that new network interface tun0 has been created
Verify that everything is fine in syslog
If you connected to VPN which forwards Internet traffic through VPN server check that IP address has been changed
OS X Client
The best client as I know is Tunnelblick. Download it, install it and start it.
Create new folder somewhere, for example on desktop
Download ca.crt, myosxclient.crt and myosxclient.key from OpenVPN server (mylinuxclient.* files are generated with ./build-key myosxclient) and copy them in ~/Desktop/vpn.
Copy sample configuration file
Adjust it
Rename folder to vpn.tblk and open it
Last command will open it and add it to Tunnelblick.
iOS Client
First of all install OpenVPN on your device.
Do everything as you did for OS X Client, but instead of renaming and opening this folder in Tunnelblick you need to copy this folder on your iOS device. I used iTunes for that: go to the tab Apps, section File Sharing, select OpenVPN and add all 4 files to this application. Do sync and after that in OpenVPN application on your iOS device you will see something like 1 new OpenVPN profile is available for import
Android Client
Install OpenVPN on your device. Again, do the same settings as for OS X Client, but instead of renaming and opening this folder in Tunnelblick you need to copy this folder on your Android device.
Use Android File Transfer tool to copy these files on your device and do import.
Links
See Also
Client software implementations
Linux Network-Manager GUI for OpenVPN
Many Linux distributions including Ubuntu desktop variants come with Network Manager, a nice GUI to configure your network settings. It also can manage your VPN connections. It is the default, but if in doubt make sure you have package network-manager-openvpn installed.
Open the Network Manager GUI, select the VPN tab and then the ‘Add’ button. Select OpenVPN as the VPN type in the opening requester and press ‘Create’. In the next window add the OpenVPN’s server name as the ‘Gateway’, set ‘Type’ to ‘Certificates (TLS)’, point ‘User Certificate’ to your user certificate, ‘CA Certificate’ to your CA certificate and ‘Private Key’ to your private key file. Use the advanced button to enable compression (e.g. comp-lzo), dev tap, or other special settings you set on the server. Now try to establish your VPN.
OpenVPN with GUI for Mac OS X
- Tunnelblick is an excellent free, open source implementation of a GUI for OpenVPN for OS X. Download the latest OS X installer from there and install it. It also is recommended by upstream which would have a alternative on their own
Then put your client.ovpn config file together with the certificates and keys in /Users/username/Library/Application Support/Tunnelblick/Configurations/ and lauch Tunnelblick from your Application folder.
Instead of downloading manually, if you have brew set up on MacOS this is as easy as:
brew cask install tunnelblick
OpenVPN with GUI for Win
Tunnelblick Ubuntu 20.04
First download and install the latest OpenVPN Windows Installer. As of this writing, the management GUI is included with the Windows binary installer.
You need to start the OpenVPN service. Goto Start > Computer > Manage > Services and Applications > Services. Find the OpenVPN service and start it. Set it’s startup type to automatic.
When you start the OpenVPN MI GUI the first time you need to run it as an administrator. You have to right click on it and you will see that option.
Tunnelblick Ubuntu 18.04
There is an updated guide by the upstream project for the client on Windows. How to add eso to steam.
References
See the OpenVPN website for additional information.
Also, Pakt’s OpenVPN: Building and Integrating Virtual Private Networks is a good resource.
Tunnelblick For Ubuntu Windows 10
Last updated 1 year, 5 months ago. Help improve this document in the forum.
